Author | Jaime Ramos
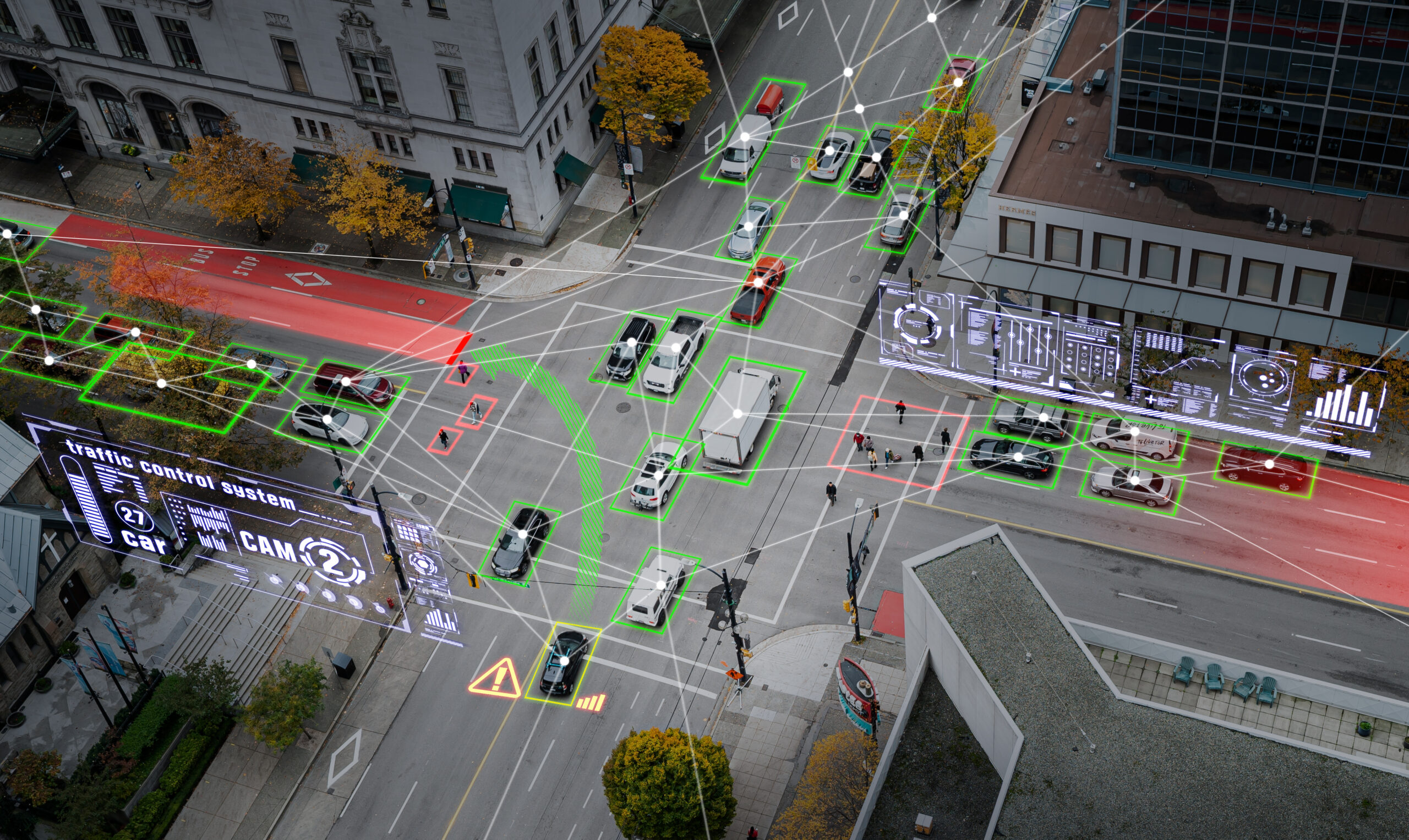
The Internet of Things (IoT) or the digital interconnection of any device promises to change the history of technology in a major way. However, it is not all good news when we talk about developments such as these. As has always been the case with any information exchange method or system, there is a risk of it being intercepted.
It is what we now know as hacking, hijacking or piracy. Information network security attacks are becoming more frequent in the public sphere. Why do they happen?
IoT: What lies behind hacking?

The security breaches that occur today tend to be essentially for financial gain. They involve hijacking data and demanding money to recover the data. These normally involve vast revenue for the affected companies.
However, there are also cases in more domestic spheres, in which the intention is to obtain users’ personal data.
The hacker reaches the data through a device, which also serves as a gateway to the network. This enables them to control other devices, just as a virus can affect various organs once it enters the bloodstream.
According to the cybersecurity firm SAM Seamless Network, in 47% of domestic network attacks security cameras are the target. Followed by smart hubs, with 15% of the attacks and storage devices connected to the network, with 12%.
Real cases of IoT attacks
Among the most prominent attacks, is the one caused by the Mirai malware capable of DDoS attacks, i.e., it hijacks devices by obtaining access credentials and modifying them.
This is what Mirai did in October 2016, focusing on routers and IP cameras, with the added ability of, once infiltrated, being able to detect, like a chain reaction, other vulnerable devices that went on to be controlled. The digital attack lasted 77 hours, involving 24,000 devices and affecting media channels such as Twitter, CNN or Reddit.
Creativity in the attacks is unlimited and, in recent years, cases have been identified that were as serious as they were famous, for example, altering the water quality in a water treatment plant demonstrations of how to manipulate traffic lights or how to control a baby heart monitor. The aim of the latter was not to obtain information about the baby’s heart rate or alarm parents with false figures, but to attack other domestic devices thanks to the vulnerability of the former.
Tips on how to protect IoT connected domestic networks

The vulnerability of the devices covered by the Internet of Things depends to a large extent on the margin of protection granted by the supplier or manufacturer. Therefore, the first recommendation is to obtain information, before purchasing a product, about the product’s real security against external attacks.
In the domestic arena, basic tips such as naming a router, establishing a local guest network for friends or family visits, changing default usernames and passwords, updating device software or disconnecting the characteristics of these that are not going to be used, can be highly effective.
In terms of industrial systems, such as those required to ensure that modern cities can operate with infrastructures based on data, the issue is more complicated. Not only technical protection measures are required, but also political measures, such as avoiding the use of external devices in secure areas and training employees to prevent the use of insecure storage devices such as a USB drive collected at the doors of an office (a method used to initiate an infection in a place that an attacker cannot get to by other means).
Before all of this, however, we need to understand why the security of the systems on which the Internet of Things is based is so important for the future of cities and why it needs to be guaranteed. There is still time to build solid defense mechanisms to prevent even more problems, the consequences of which may be hard to predict given the potential of IoT to influence our lives.
Images | iStock/Pheelings Media), iStock/Igor Kutyaev, iStock/gorodenkoff